Analyzing Latest WhatsApp Scam Leaking AWS S3 Bucket
This is a quick blog about an amazon scam going on WhatsApp. In search of data, I found the S3 bucket which is publicly available. Since these scammers use victims’ data for personal use, I will be using their data for personal research.
Let’s begin the story of how it was possible to find data of scammers. This data may not contain the personal details of attackers but it can help to analyze the coding pattern and different source codes which are used by this group for multiple phishing attacks. Here I have mentioned two links there are chances that many more links are present.
Do not visit or click on the link and submit personal information.
Received the link in the WhatsApp group about the recent phishing scam.
Link 1: http://amaxxxxxx.xyz/amazonhz/tb.php?v=ss1616659
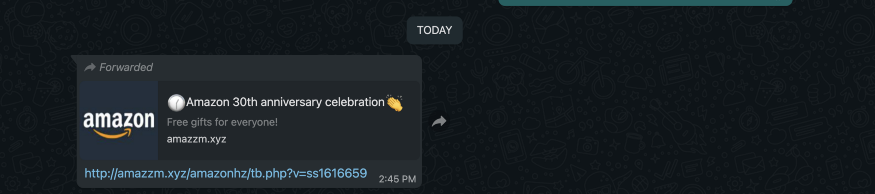
Link 2: https://ccwexxxxx.xyz/amazonhz/tb.php?v=ss1616675
The above links have been changed so that no one clicks unintentionally.
Let’s Jump In
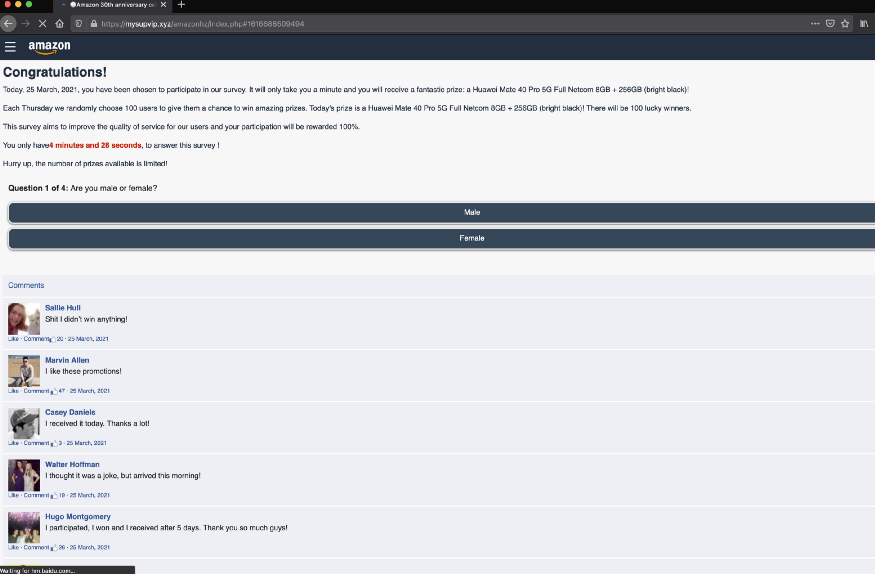
- Click on the scam link in incognito mode, which starts the set of questions. These questions can be used to guess the age and gender of victims.
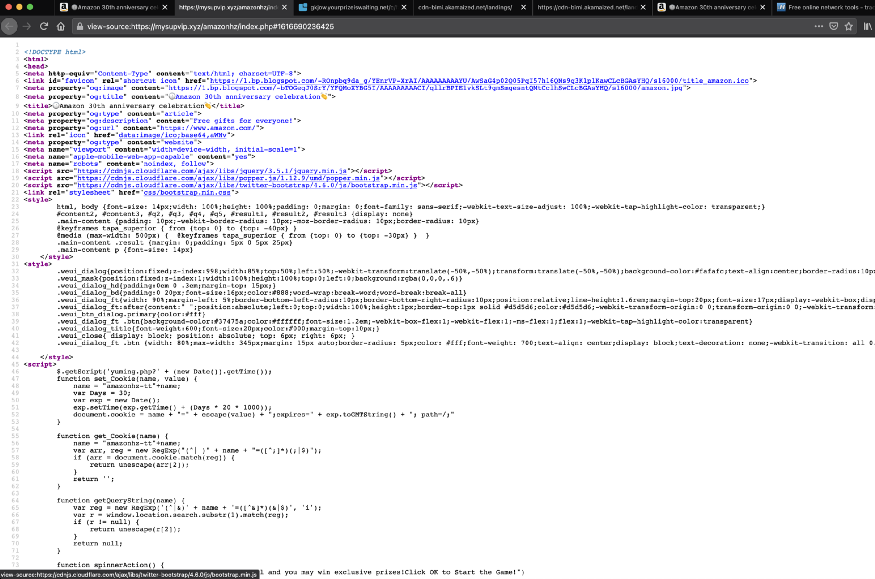
2. Check the source code, there are multiple chances of DOM XSS here, if you find one update the comment below.
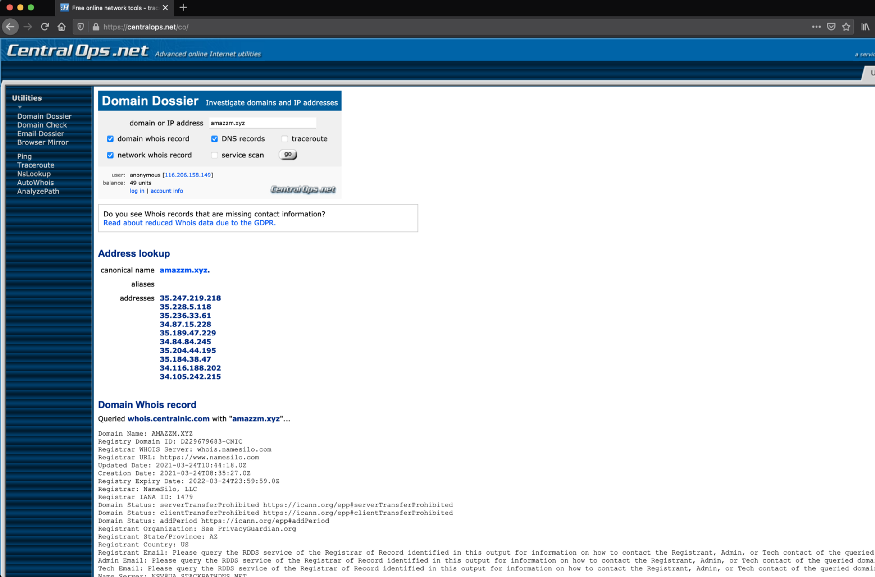
3. Check the whois for the website. It shows Google LLC, which means it should be a GCP instance.
4. Fill the form completely. Now proceed and win the Huawei phone, website wants to share this on WhatsApp.
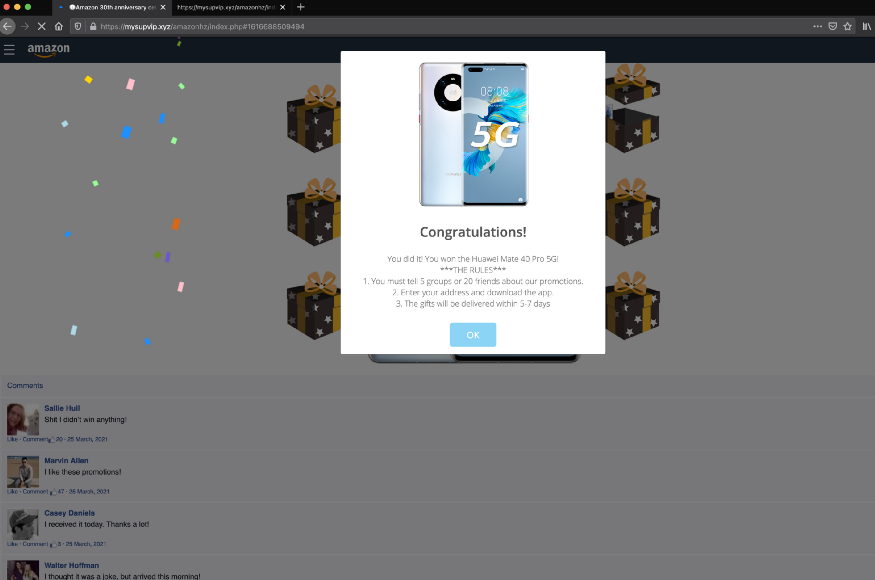
Then sharing page arrives. This sharing ensures that the scam never dies.
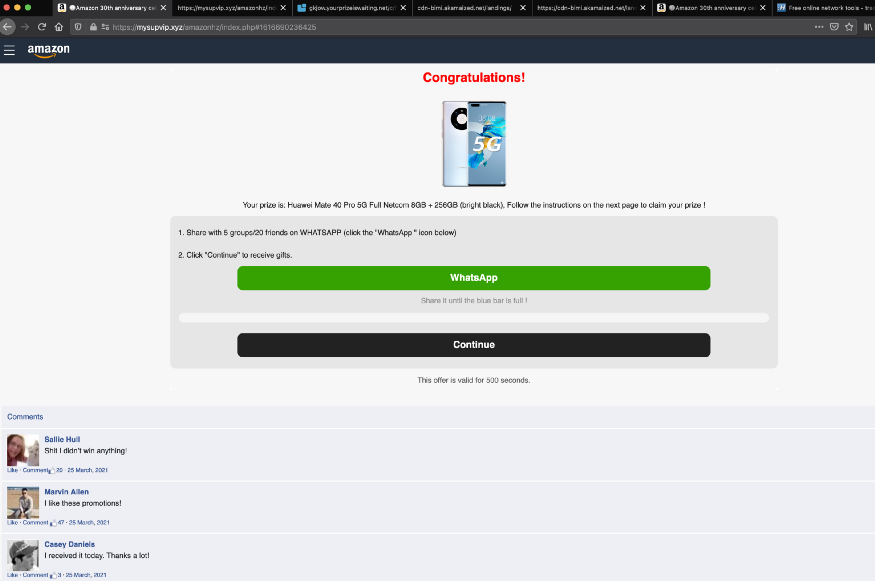
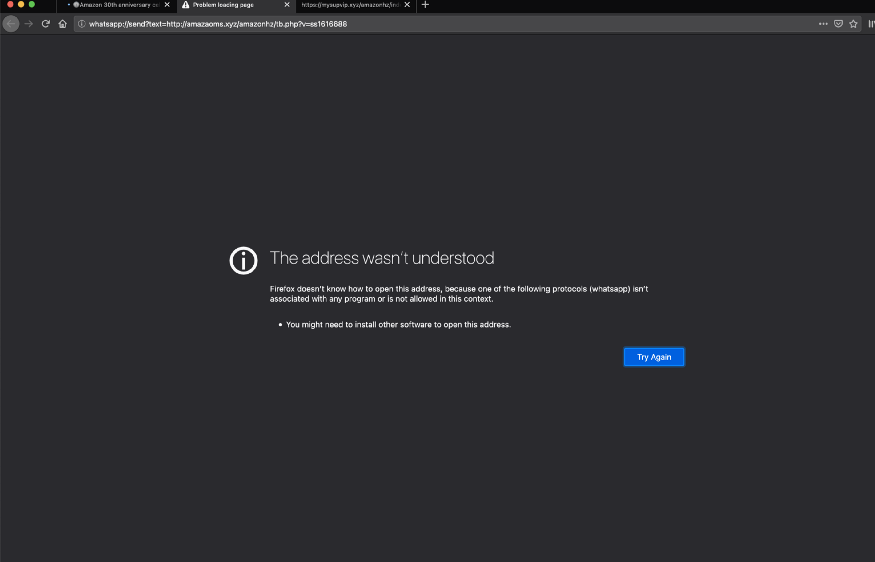
Here browser doesn’t know whether the link is shared or not. Click on complete registration.
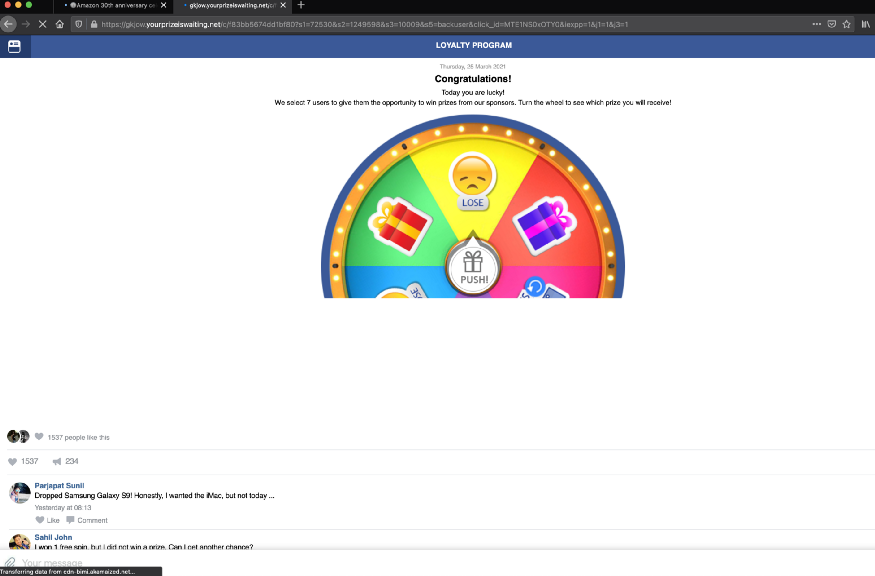
You will be redirected to a new phishing domain: https://gkjow.yourprizeiswxxxxxxxx.net/c/f83bb5674dd1bf80?s1=72530&s2=1249598&s3=10009&s5=backuser&click_id=MTE1NS0xOTY0&iexpp=1&j1=1&j3=1
Sometimes page was redirected to another phishing page.
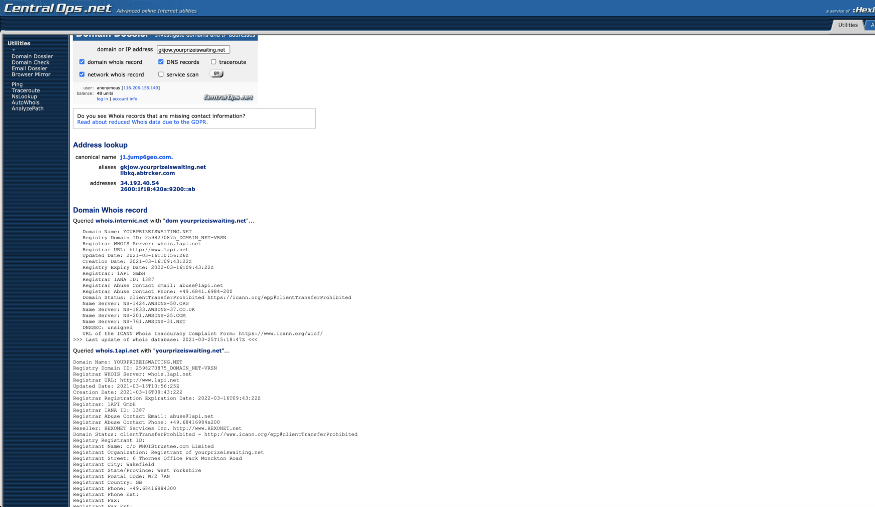
On checking the whois for the new website, it shows it is hosted on AWS cloud.
Hereafter clicking ok and try two failed attempts, the third attempt will show the prize won in $$$$.
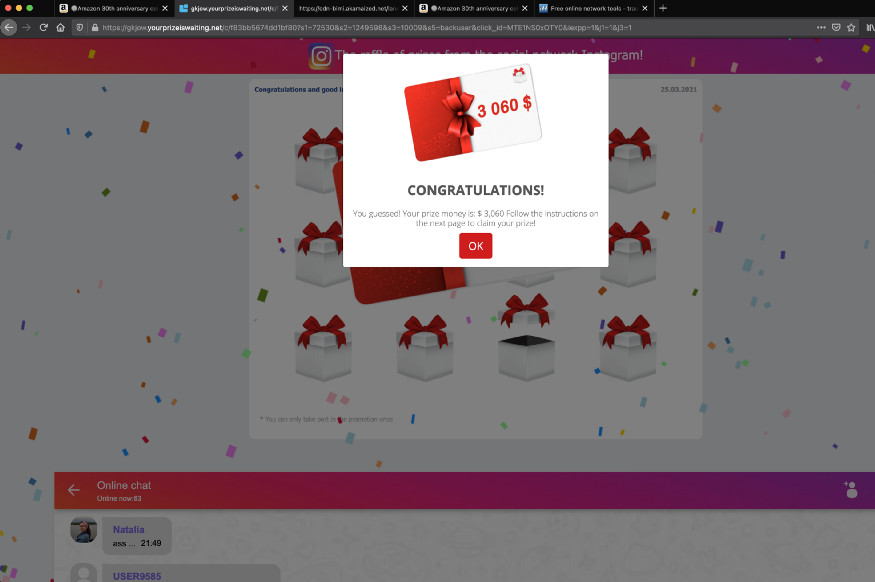
Click ok and check the source code for more information.
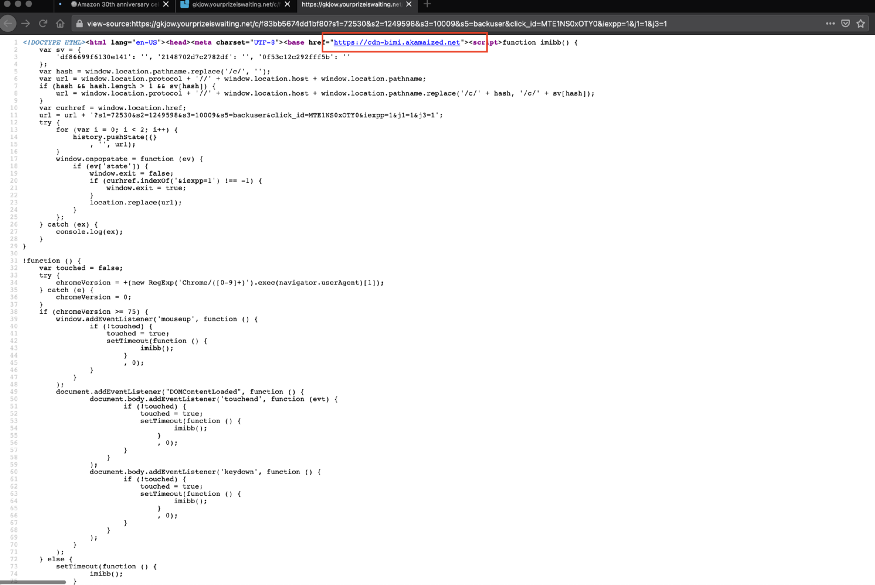
In the source code, one domain in the base href tag is https://cdn-bimi.akamaized.net.
On visiting the link: https://cdn-bimi.akamaized.net, it shows 404.
But after poking in the source code, check the image tag loading images. There is a tag pointing to /landings/206101/1614865415/images/map.png
Click on the image, it shows a very small icon. But let’s try something else.
On removing the last part (image-name) from the URL, if directory listing is enabled all the directory structure should be visible.
But it shows 404. We couldn’t find this page
But on removing the 206101/1614865415/images/map.png from cdn-bimi.akamaized.net/landings/206101/1614.. It shows something.
This is listing the S3 bucket because the listing is enabled.
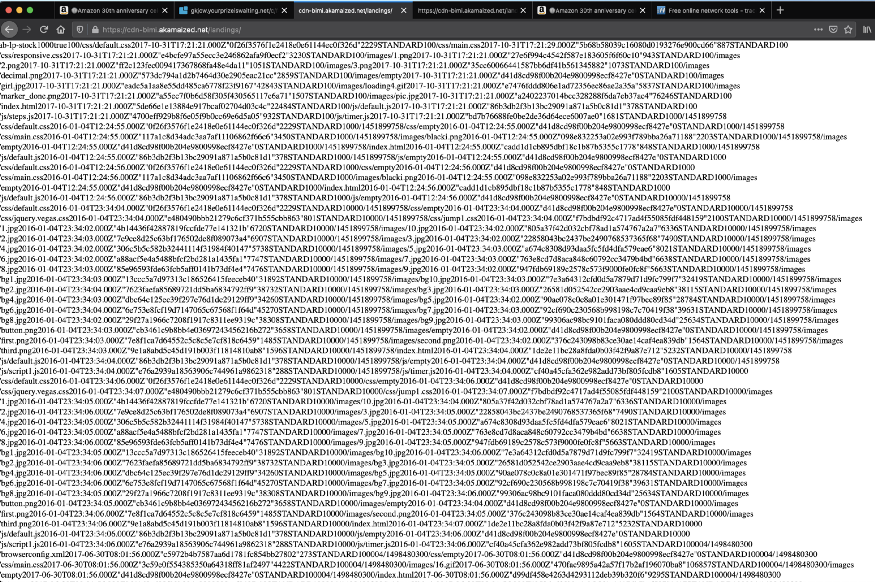
Now try to PUT, DELETE and GET operation via the AWS CLI.
Let’s create a sample by
#touch sample.txt
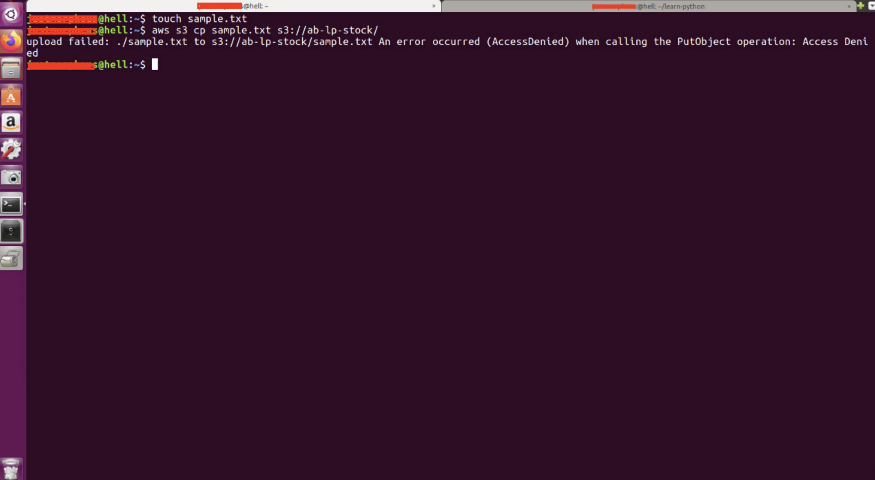
Now upload the sample.txt by copying it to the S3. It shows access denied.
#aws s3 cp sample.txt s3://ab-lp-stock
Then try to move the sample.txt to the S3 bucket
#aws s3 mv sample.txt s3://ab-lp-stock
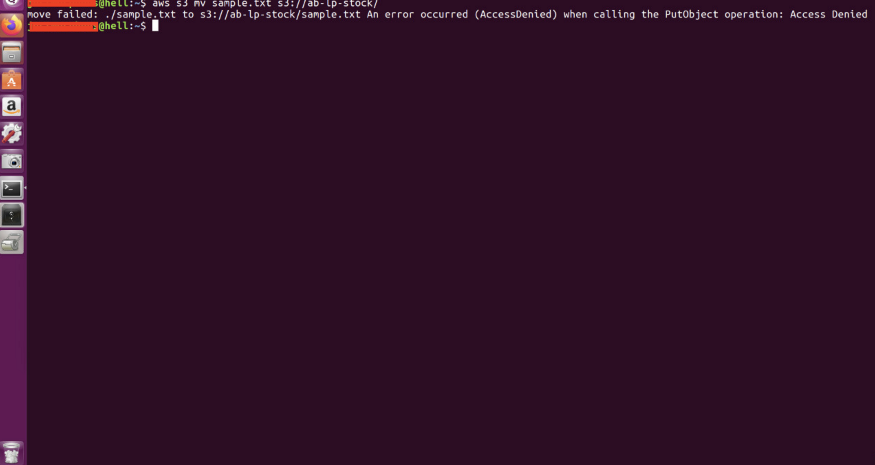
It is not possible to move or copy the file into the S3 bucket.
Now try to list the files, listing is enabled.
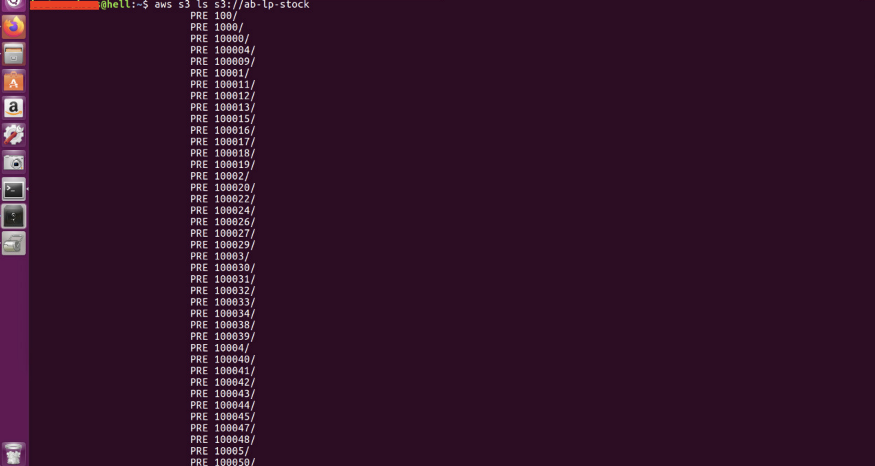
Let’s download the data for further analysis because this will help in understanding the coding as well as javascript used for spamming.
Let’s use the sync command to download.
#aws s3 sync s3://ab-lp-stock .
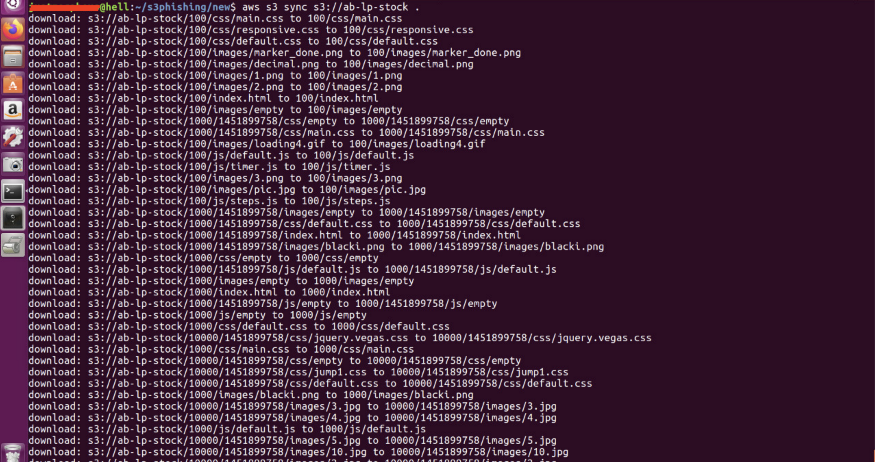
Downloaded more than ~35 GB of data and now it’s time to disconnect. Maybe try downloading on the cloud.
We could have also used shodan to get more details about the IPs.
Note: This fraudulent website might be asking users to enter their personal details and send the same link to 5 friends or groups, by sharing they ensure that the scam is continued. Never ever submit your personal data. Many of these sites ask for personal information and add timers to the webpage to give users a sense of urgency while they enter their information. Providing personal information on these websites can lead to loss of personal information and financial fraud, so users are advised not to download any apps, or enter their information on any unknown websites, especially after clicking on a link they received online.
Also never ever visit these websites via mobile browsers as they are also prone to 0 days attacks. These 0-day attacks can be leveraged to perform the more sophisticated attacks.
This research is just to uncover that how spammers try to phish the users and what are some possible scenarios by which we can get to know about the scammer’s data.
Till the next time, we say goodbye !!
